Affiliate Disclosure: VPNexp.com is reader-supported. We may earn a commission if you purchase a VPN through links on our site. This does not affect our rankings or recommendations.
Three Tools, Three Very Different Purposes
In the digital age, more people are becoming aware of privacy tools like VPNs, proxies, and Tor—but many don’t understand how they differ or when to use which. At a glance, all three can mask your IP address or route your traffic differently, but their goals, privacy guarantees, and performance characteristics are distinct. Understanding these differences helps you make informed decisions about protecting privacy, bypassing restrictions, and staying safe online.
Table of Contents
Quick Comparison: VPN vs Proxy vs Tor
Below is a high-level overview of the major differences before digging deeper:
| Feature | VPN | Proxy | Tor |
|---|---|---|---|
| Encrypts Traffic | ✅ Full device encryption | ⚠️ Usually none | ✅ Multi-layer onion encryption |
| IP Address Hidden | ✅ Yes | ⚠️ Yes (app/browser only) | ✅ Yes (exit node IP) |
| Anonymity Level | Moderate | Low | High |
| Speed | Fast – Moderate | Fast | Slowest |
| Typical Use Cases | Everyday privacy, streaming, security | Basic access or IP masking | Maximum anonymity, censorship circumvention |
What Is a VPN?
A Virtual Private Network (VPN) encrypts all your internet traffic from your device and routes it through a remote VPN server. This process creates a secure tunnel that prevents outsiders—like your ISP or anyone on a public Wi-Fi—from seeing your traffic or your real IP address.
Many reputable VPN providers also implement strong encryption (e.g., AES-256, WireGuard) to protect your data and uphold no-logs policies, which limits what they store about your activity.
VPN Pros
- Device-wide encryption and privacy: All your internet activity is routed securely.
- Good balance of privacy and speed: Faster than Tor while still hiding location and traffic details.
- Useful for streaming, travel, and public networks: Helps bypass region locks and Wi-Fi risks.
VPN Cons
- You must trust the VPN provider’s privacy policies.
- Not designed to deliver full anonymity like Tor.
Popular VPN options include NordVPN, Proton VPN, and IPVanish.
What Is a Proxy?
A proxy server acts as an intermediary between your device and the internet: your connection to a website appears to come from the proxy’s IP, not your own.
Proxies are commonly used for simpler tasks like bypassing basic web filters or changing your IP address in a specific browser or application. Proxy configurations might include HTTP, HTTPS, or SOCKS proxies, with varying speeds and compatibility.
Proxy Pros
- Lightweight and often fast: Less overhead than VPNs or Tor.
- Good for specific apps or tasks: Can be set on a single browser or service.
Proxy Cons
- No encryption by default: Traffic may be visible to networks and ISPs.
- No system-wide protection: Only covers configured apps.
- Low anonymity: Easy to trace a proxy connection back to you.
What Is Tor?
Tor (The Onion Router) is an anonymity network that sends your traffic through multiple encrypted relays (entry, middle, and exit nodes) to conceal who you are and where your traffic originates.
Instead of a single intermediate server like a VPN, Tor’s multi-layered “onion” routing means that no individual relay knows both your identity and the destination of your traffic. This makes Tor extremely difficult to trace but also slower than VPNs and proxies.
Tor Pros
- High anonymity: Difficult to associate traffic with your real identity.
- Free and decentralized: Supported by volunteers around the world.
- Strong censorship resistance: Valuable for users in restrictive regions.
Tor Cons
- Slow performance: Traffic routed through several relays adds latency.
- Compatibility limitations: Some services block Tor exit IPs.
- Not ideal for everyday use: Best suited for specific anonymity needs.
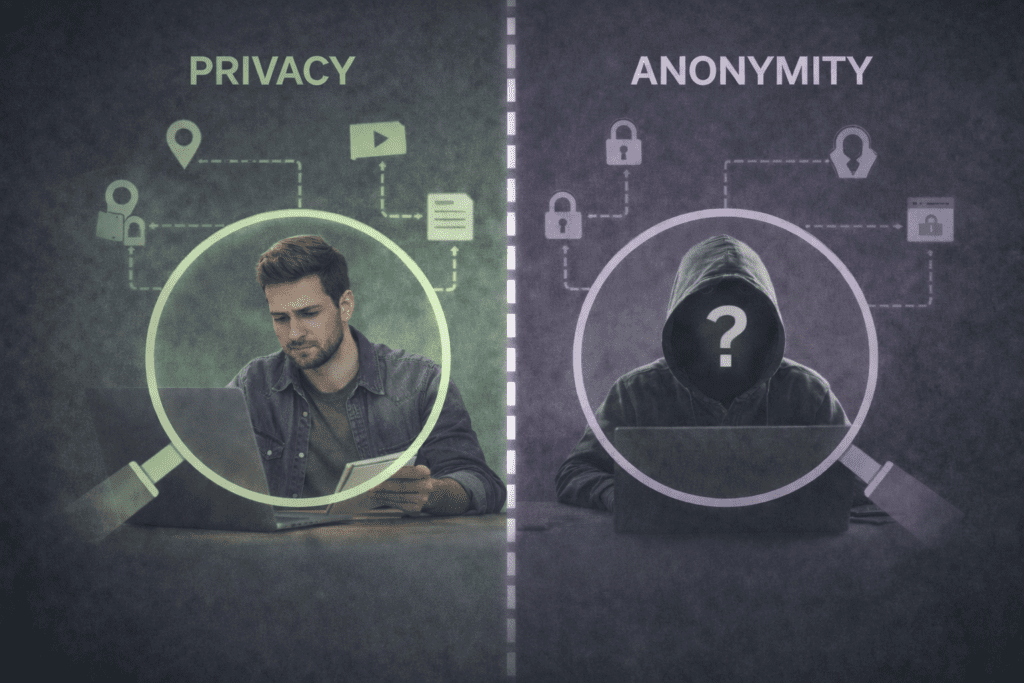
Privacy vs Anonymity: The Core Difference
Although privacy and anonymity are often used interchangeably, they’re distinct. Privacy means obscuring what you do online, such as hiding traffic or location from observers. Anonymity goes further by making it extremely difficult to link that activity back to your identity. VPNs primarily enhance privacy, while Tor emphasizes anonymity. Proxies offer minimal privacy and even less anonymity.
Which One Should You Use?
Use a VPN If…
- You want everyday privacy and security on public Wi-Fi or when traveling.
- You need fast speeds and broad application compatibility.
- You want to access region-restricted content, like streaming services.
Use a Proxy If…
- You’re performing lightweight or specific tasks that don’t require security.
- You only need to change an IP for a single app or browser.
Use Tor If…
- Anonymity is critical (e.g., journalism or activism).
- You’re in a high-censorship environment and want to bypass restrictions.
- You don’t need high performance or streaming speeds.
Can You Combine VPN, Proxy, and Tor?
Yes—and some users do stack them for layered protection—but this comes with trade-offs: complexity, slower speeds, and sometimes confusing privacy guarantees. For example, using a VPN with Tor can help hide your Tor usage from your ISP, but the VPN may still see your traffic.
Key Takeaways
- VPNs balance privacy and performance for everyday use.
- Proxies offer simple IP masking with minimal protection.
- Tor offers the strongest anonymity but at slower speeds and with limitations.
FAQs
Is a VPN the same as Tor?
No — VPNs focus on privacy and routing your traffic through a secure server, whereas Tor focuses on anonymity through multi-layered encryption across volunteer relays.
Can a proxy replace a VPN?
Not really — proxies don’t typically encrypt your data or protect all your traffic like a VPN does.
Does Tor make you completely anonymous?
Tor offers high anonymity, but nothing is 100 % foolproof, and some risks remain if traffic exits through malicious exit nodes.
Which is safest for public Wi-Fi?
Use a reputable VPN — it provides encryption across all apps and devices on that network.
Can websites still track you when using these tools?
Yes — if you log into accounts, accept cookies, or use browser fingerprinting, tracking can still occur even behind a VPN, proxy, or Tor.
Sources
- “Tor vs. VPN” – TheBestVPN.com Torism vs VPN Privacy Explained
- “VPN vs Proxy vs Tor: What Are the Differences?” – Avast Avast VPN Proxy Tor Guide
- “Tor vs. VPN: What’s the difference” – Norton Norton Tor vs VPN Comparison
- “VPN vs Proxy vs Tor Comparison Overview” – Batten Cyber Batten Cyber VPN Proxy Tor
- “VPN vs. Proxy vs. Tor: Key Differences Explained” – Ivacy Ivacy VPN Proxy Tor Differences